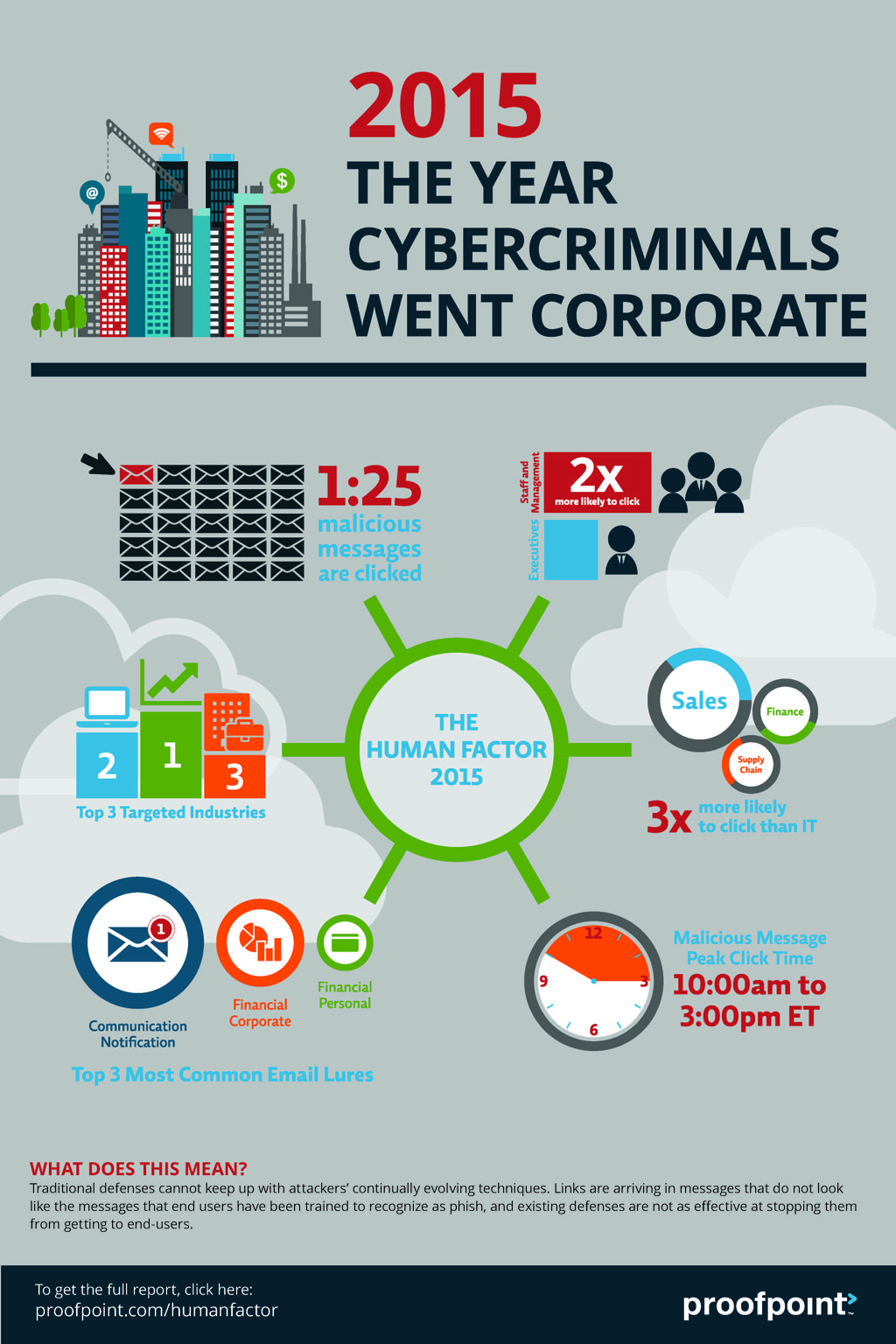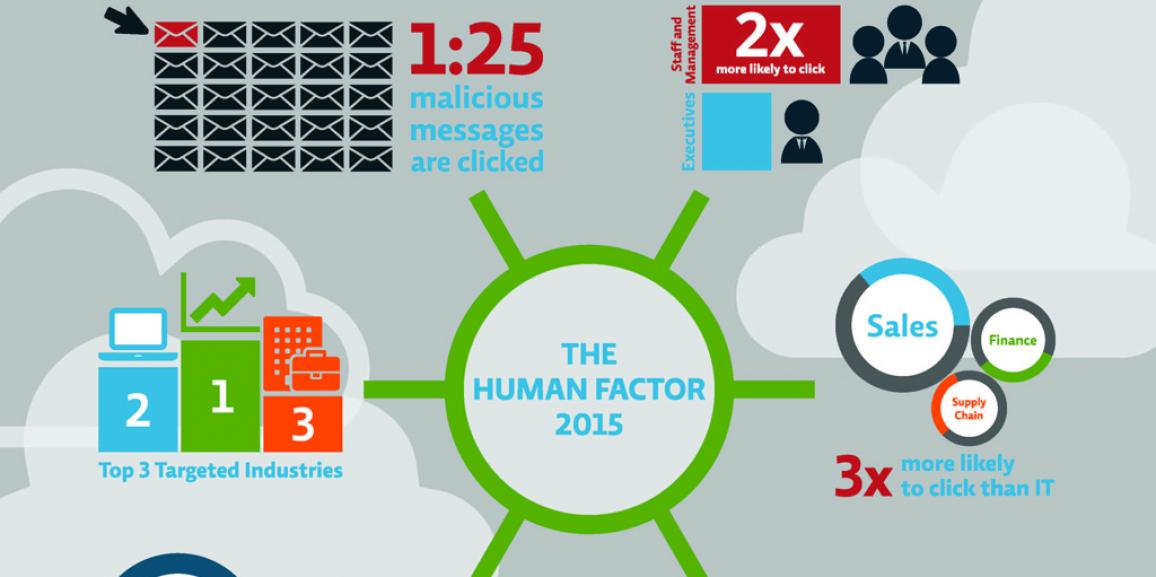
Traditional defenses cannot keep up with attackers’ continually evolving techniques. Links are arriving in messages that do not look like hte message that end users have been trained to recognize as phish, and existing defenses are not as effective at stopping them from getting to end users.