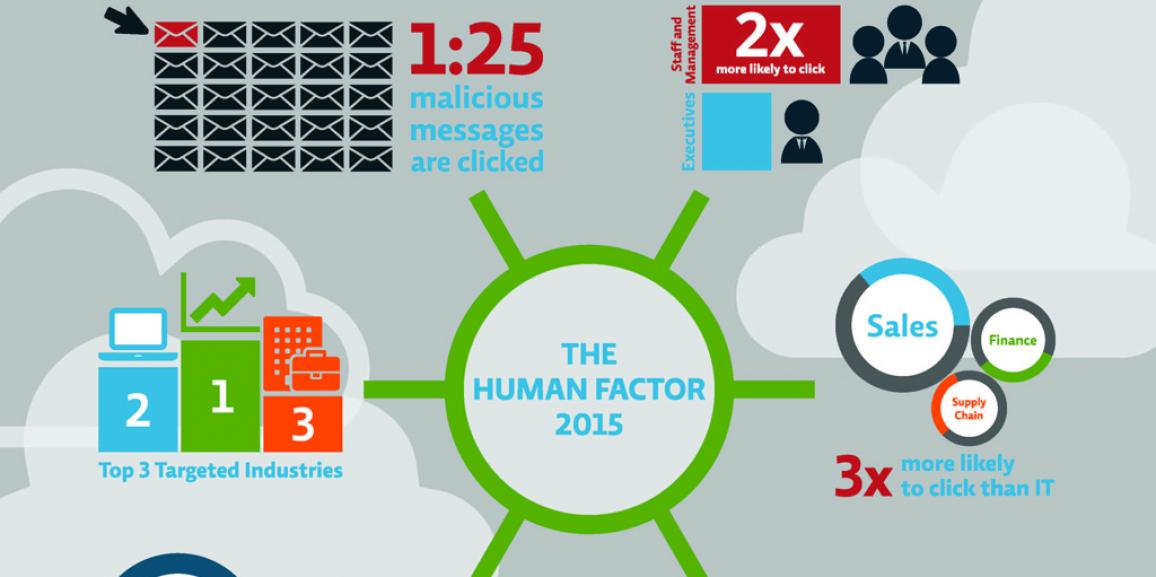
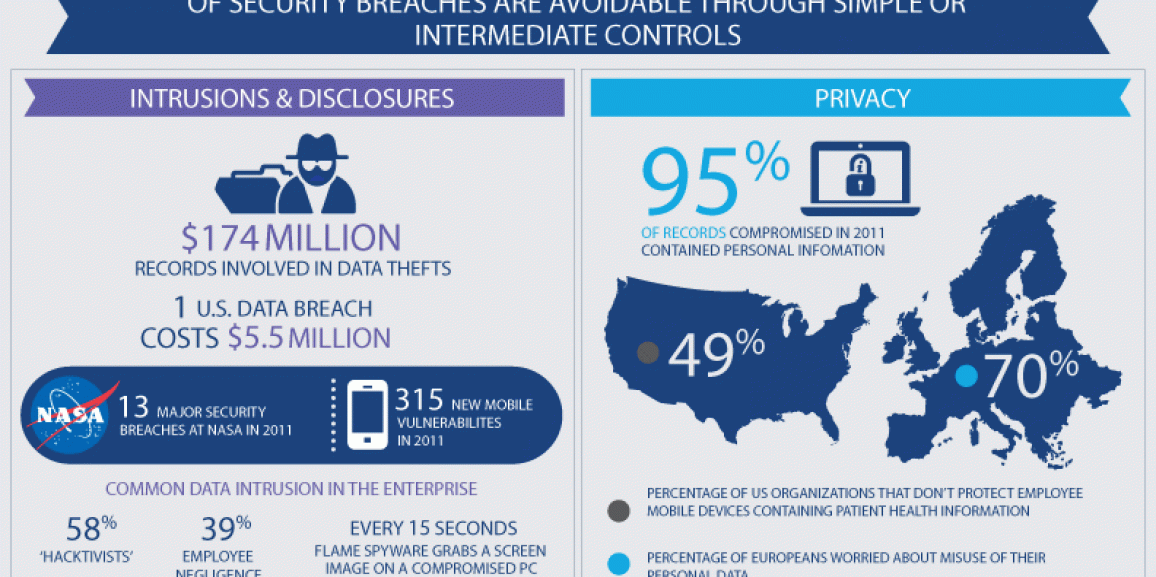
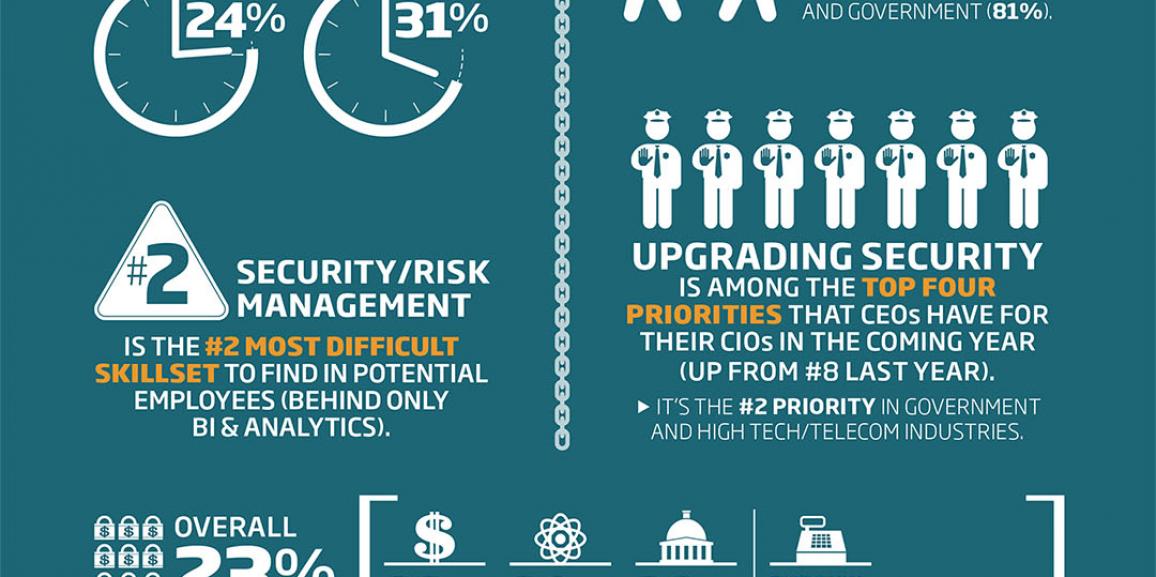
SplashData has announced the 2015 edition of its annual “Worst Passwords List”, which highlights the insecure password habits of Internet users. As you can imagine, passwords such as “123456” and “password” still top the list as the most frequently used passwords. However, the list shows a level of being affected by trends in popular culture, […]