Learn to effectively manage, secure and optimize enterprise information.
- How do you govern and manage information?
- How do you balance confidentiality, availability and integrity of enterprise information?
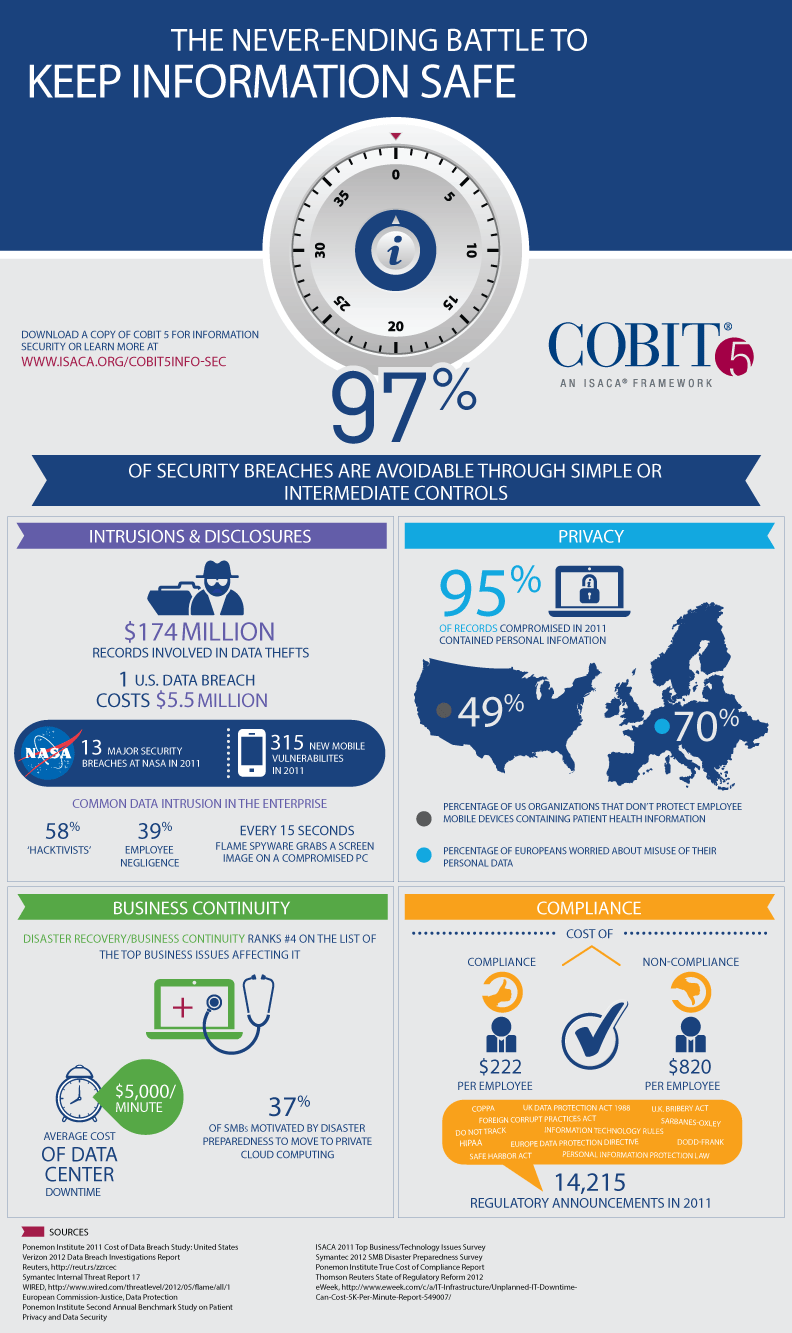
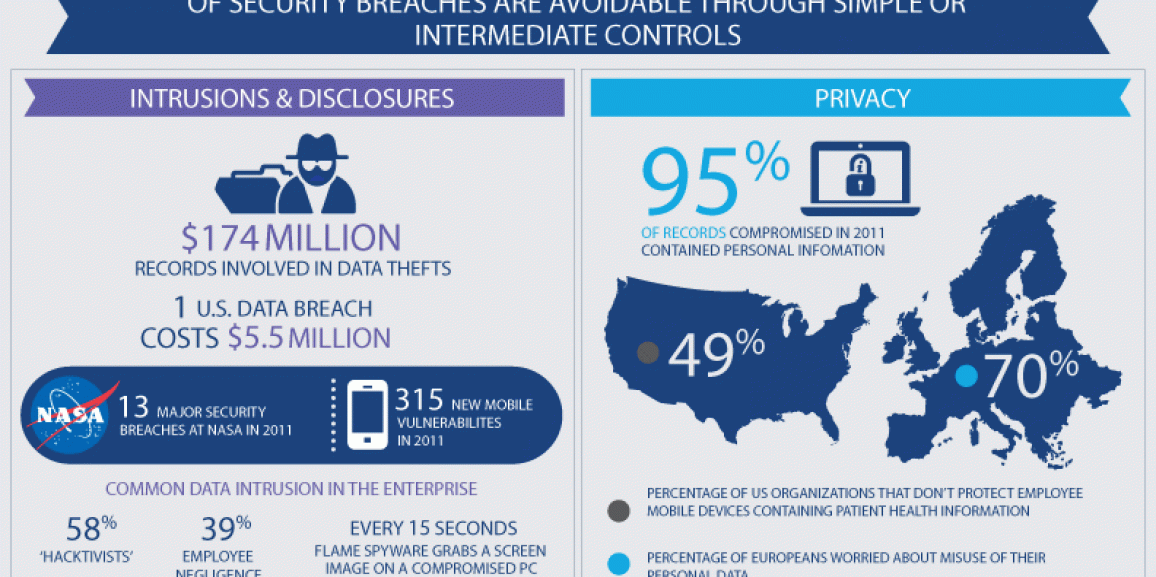
Information security is essential in the day-to-day operations of enterprises. Enterprises need to ensure the confidentiality and integrity of their information, while simultaneously providing availability to those who need it.
Information security professionals work to protect enterprise information in a changing environment. The regulatory and threat landscapes continue to evolve, requiring enterprise leaders to be knowledgeable on business issues such as privacy and governance while maintaining awareness about emerging technologies and the accompanying threats.

At a time when the significance of information and related technologies is increasing in every aspect of business and public life, the need to mitigate information risk is constantly intensifying. Increasing regulation adds to the complexity of information security. A main issue many enterprises face today is the diversity of all types of privacy legislation and regulations, which makes it very difficult to select one privacy solution. The use of a framework enables effective consideration and balancing of multiple stakeholders needs related to privacy in this complex legislative and regulatory area.
COBIT 5 helps business leaders govern privacy, work out the risks around privacy, ensure proper security management and ensure auditing of privacy measures are in place. The framework helps enterprises to direct, monitor and evaluate the privacy vision and requirements based on the business needs, whereas the executive management and all employees involved with privacy-related information should focus on the plan, build, run and monitor approach.
The COBIT 5 framework complements existing security standards and frameworks by providing a holistic approach to identifying threats against data privacy, security and compliance and by addressing residual risks in effective and efficient ways.